
Latest attacks prove there are no depths to which scammers won’t sink in order to steal from victims.
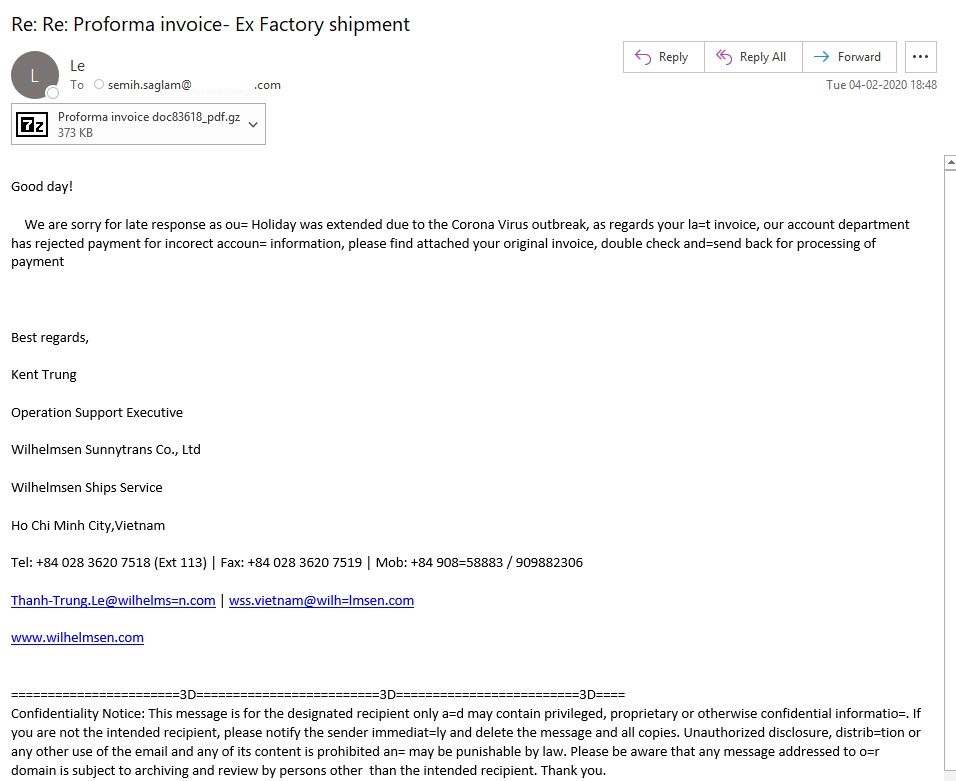
The Comodo Cyber Security research team recently discovered two opportunistic malware attacks which hope to take advantage of people’s fears and sympathies over the Coronavirus. The attacks use the classic method of spamming victims with an ostensibly trustworthy email containing malicious attachments and links. The first message reads “We are sorry for late response as our Holiday was extended due to the Corona Virus outbreak, as regards your la=t invoice, our account department has rejected payment for incorect accoun= information, please find attached your original invoice, double check and=send back for processing of payment”.
The attached ‘invoice’ is, of course, malware. In this case it is a banking trojan called ‘Lokibot’ which hoovers sensitive data such as usernames and passwords from the user’s browser. The second email has a Corona-related click-bait link which reads: “BREAKING NEWS: Military Source Exposes Shocking TRUTH About Coronavirus and the 1 thing You Must Do Before It’s TOO LATE”. Again, clicking the link causes the installation of the Lokibot malware.
As you’re undoubtedly aware by now, the Coronavirus is a deadly infection that is spreading fast around the world and has caused widespread public fear. Cybercriminals are trying to cash-in on the public interest around the virus by lacing the text of their phishing emails with Corona-related information.
The Loki emails contain a malicious attachment which has the extension “.pdf.gz”, the attacker obviously hoping people assume it is a PDF and don’t notice the .gz extension. The file installs the Lokibot banking trojan if the user opens the attachment. The trojan harvests sensitive information stored in internet browsers, including bank login details and other system information, which it then sends back to the malware authors.
The following image is a screenshot of the first email which contains the Lokibot attachment:
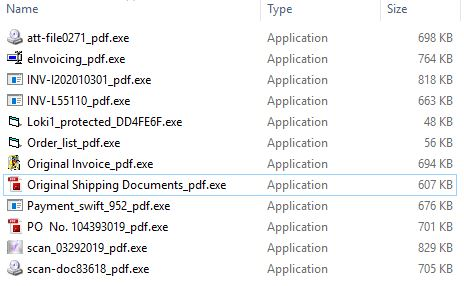
The .gz attachment contains the following malicious executables:
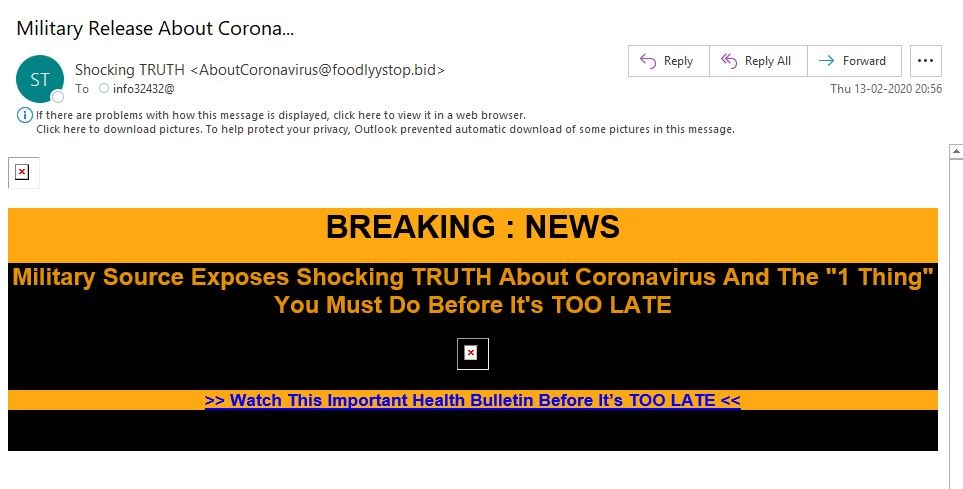
The second phishing mail takes a different approach, attempting to goad users into clicking a link by promising groundbreaking information about the Corona virus. The mail contains a striking image with the following headling:
“BREAKING NEWS Military Source Exposes Shocking TRUTH About Coronavirus And The “1 Thing” You Must Do Before It’s TOO LATE”
The emails come from seemingly authoritative email addresses such as the following:
AboutCoronavirus@foodlyystop.bid, AboutCoronavirus@nanopower.us, AboutCoronavirus@steeldefennse.us, MilitaryExposes@foodlyystop.bid, MilitaryExposes@steeldefennse.us, ShockingTRUTH@foodlyystop.bid, ShockingTRUTH@steeldefennse.us, CoronaProtection@guntracker.buzz, Coronaprotection@savecertified.us, VirusProtection@guntracker.buzz
However, clicking the link in the mail causes the installation of the Lokibot malware. Here are the signatures of the malicious files which form the Lokibot malware package:
att-file0271_pdf.exe d3d609c2007850de58dd95dc573506f1f6c035a8
eInvoicing_pdf.exe 5b6b7b2c91205fb530129cfdce98b02e61a240d3
INV-I202010301_pdf.exe 57f70011c2537cabc9e19ac25cad3a5327969154
INV-L55110_pdf.exe e12f1516bed85538db1a1760007039fc87f3c416
Loki1_protected_DD4FE6F.exe e786661aa8fbe82a7b515b5e5cc623f4141a7fc9
Order_list_pdf.exe 53a2219bd0af7af19a1da619354eeb989bb91191
Original Invoice_pdf.exe 80c3f9968ecdc33d817040c781e075a19a681cdf
Original Shipping Documents_pdf.exe b7013f3cd7db4b82f122ca90e78dd7168910ea09
Payment_swift_952_pdf.exe 29d7fb10e7365c9a70fcc99a4154eaf462f9bf63
PO No. 104393019_pdf.exe 292b75ec0222df1fd19b85a72be1980029d94e48
scan-doc83618_pdf.exe 809ceaf0ceef8d418f4782f1a2bf3f9ff502f865
scan_03292019_pdf.exe 76ed1dab029bb1081e01ee8764310e61a7580c94
Tips to avoid falling prey to malware spammers
Never click links in an email – ever. Even if it looks like a legit message from a company you do business with, you should ignore the link in the mail and instead log into your account through your browser or the company’s app. If it’s a genuine message, then the same message will be waiting for you in your online account.
Some spam emails are very professional looking – they have your name correct, they have the right logos, the message content looks like previous emails from the company, and they even have a legal disclaimer at the bottom. For example, say you get a mail that looks like its from PayPal, stating there is a problem with your account and that you should click the following link to update your details. The login page it sends you to is fake. If you enter your username and password then you have handed your account details to the hacker, who can login to your account and drain your funds at will.
If you receive a convincing looking mail and want to put your mind at ease, simply close the mail and separately login to your account through your browser by clicking your usual bookmark (or by typing the company’s URL in the address bar). Any genuine message from the company will also be available in your online account. If you can’t find any mention of it in your account, then the mail is bogus. In fact, you should follow this process for all email communications, even for real messages from the company in question, just to get yourself into the habit.
Don’t open email attachments. Online criminals often attach files to messages that have extensions like .pdf or .doc. In reality, they are viruses or trojans which will infect your system, steal your confidential data, add your computer to a bot-net, or worse. Instead, follow the same process as described in the previous point. Ignore the attachment and the mail, and simply login to your account via your browser or the company app. If the message is legit, it will also be in your online account.
Look out for bad grammar. As with almost all spam-malware, the Coronavirus mails contain several spelling and grammar mistakes. Simply put, large organizations like banks and other major businesses would never send out such a shoddily written, unprofessional looking mail to their customers. If the mail looks like it was written by a child, then it’s a virtual dead-certainty that its spam-malware.


 (22 votes, 4.18 / 5
(22 votes, 4.18 / 5
