Latest Comodo Antivirus Blog Updates
Why You Need Antivirus Software for Your Android Devices
Introduction Viruses attack your operating system in different ways, and all operating systems are vulnerable, including Windows and Android. While the early concern of infection was limited to desktop computers, recent malware alerts for Android mobile devices are growing harder…
Rootkits or Keyloggers can Hide on a Graphics Card and Gain Access to your Computer
What is a Graphics Card Any videos, images or pictures that you see on your computer screen are managed by certain graphic components. Such graphic components are aligned in a different card, which is plugged into a specific provision on…
Multinational Coalition Fights Banking Trojan Ramnit
A multinational coalition of organisations led by Europol’s European Cybercrime Center (EC3) has working successfully to disrupt the Ramnit malware family. Ramnit is a Computer worm that affects Windows users. Ramnit was first detected in 2010, attaching itself to executable…
Beware Rogue Antivirus!
An all too popular scam among cybercriminals is to trick website visitors into downloading fake antivirus software by warning them that there computer is already infected. They will pretend to do a scan that comes up with all sorts of…

9 Tips to Avoid Malware Hell!
In today’s dangerous threat environment, you have to be proactive to keep your computer safe. Hackers are spreading malware that will make your life a living hell. Here are 9 tips to keep in mind that will keep you out…
How to Keep Your Email Safe
Email has become an essential tool for communication with organizations and among friends. Criminal hackers and other snoopers are eager to compromise email accounts to learn about you and to infect you with malware. Here are a few tips on…

The Weakness of Conventional Security: Unknown Threats
Most organizations have faced data breaches at some, with the number of victims growing daily. It does not matter how big or small the organization is, everyone is now a target. In recent years, enough high profile retailers have been…

Is Your Weak Password Your Weakest Link?
Every time you turn around these days you are asked to setup a user id and password. Mostly for web sites, but for telephone systems and computer access too. Keeping track of them all can be a challenged and it…
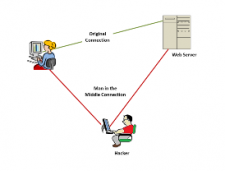
The Man in the Middle: He is Coming After You!
When you were a kid, presuming that you have indeed grown up, did you ever play the game “Man in the Middle”? That is where two players play a game of catch with a large ball, but they must throw…

Do You Have Android Malware on Your Mobile Device?
Android is the most popular operating system for smartphones, making it an inviting target for hackers and scammers. In fact, 97% of the malware identified for mobile devices are designed to attack android smart phones. Do you have Android Malware…

